For Which of the Following Purposes Would You Use Sha-1
The shasum command shows the SHA-1 hash of a file by default. The SHA-1 hash for the resource.
All major browsers are currently issuing.

. With SHA-1 you will get about 6 MBs using the full CPU. This is the encryption technique being used mainly today which makes use of the hash function named Keccak. Users report that the database on the main server cannot be accessed.
Oct 19 2016 at 1723. Cybersecurity Essentials 11 Chapter 2 Quiz Answers 100 2018 What are two common hash functions. What service determines which resources a user can access along with the operations that a user can.
Secure Hash Algorithms also known as SHA are a family of cryptographic functions designed to keep data secured. The Council has advised against the use of SHA-1 for authentication purposes. VA Special Home Adaptation SHA Grant.
Essentially this means that if you do not use all the money right away you can access the funds again in the future. Drag the protection types to match them with their categories of TCSEC Category A. HOTSPOT You write the following Java program for Munsons Pickles and Preserves Farm.
To access them launch a Terminal window. The hash function then produces a fixed-size string that looks nothing like the original. The SHA-1 hash algorithm plays a critical role in securing SSL communications where it is used to verify a certificates integrity.
The algorithm is generally employed to transform large blocks of data into 160 bit long values hashes each being unique to the encrypted content. Not listed is RSA which is commonly implemented to secure credit card transactions. The three SHA algorithms are structured differently and are distinguished as SHA-0 SHA-1 and SHA-2.
This hash value is known as a message digest. But someone needs to notify the next of kin because new research from Venafi Labs shows that 1 in 5 of the worlds websites are still using certificates signed with the vulnerable secure hash algorithm SHA-1. Which of the following reflects the level of availability you require.
Federal Information Processing Standard and was designed by. A hash algorithm has the capability to. BCrypt SCrypt PBKDF2 Argon2 etc Separately from that there are reasons to use SHA-2 over SHA-1 and computation speed is not a significant to that comparison.
Reserved for systems that have been evaluated but do not meet requirements to belong to any other categoryB C D. Its not like these organizations didnt know SHA-1 was a problem. Shasum -a 1 pathtofile.
This message digest is usually then rendered as a hexadecimal number which is 40 digits long. A revoked certificate is no longer valid for the intended purpose and a new key pair and certificate will need to be generated. Line numbers are included for reference only.
You are trying to determine the appropriate level of high availability for a server. SHA-2 has several variants all of which use the same algorithm but use different constants. As early as July 2011 PTS POI Security Requirements warned and then disallowed SHA-1 for digital signatures.
Choose two Blowfish ECC RC4 SHA MD5 RSA Explanation. Suppose that you want to hash some data eg. Top 1 IT Exam Answers and Certifications Preparation for 2022.
SHA-256 for example sets additional constants that define the behavior of the SHA-2 algorithm one of these constants is the output size 256. Which of the following would you use to verify certificate status by receiving a response of good revoked or unknown. The Secure Hash Algorithm defined in Federal Information Processing Standard 180-1.
Hash Values have different uses. SHA and MD5 use use complex mathematical algorithms to compute hash values. Comments about specific definitions should be sent to the authors of the linked Source publication.
SHA-1 used in digital signatures is not considered Strong Cryptography for purposes of PCI DSS or P2PE. One of the main uses of Hash Values is to determine the Integrity of any Data which can be a file folder. An algorithm that consists of bitwise operations modular additions and compression functions.
The truncated versions of these values include SHA-224 SHA-384 and SHA-512 and SHA-224 or SHA-256. Important Hash value Algorithms MD5 SHA-1 and SHA-2. TemplateInfobox cryptographic hash function In cryptography SHA-1 is a cryptographic hash function designed by the National Security Agency NSA and published by the NIST as a US.
SHA-512 will give you no more than 15 MBs on the same machine. The 256 and 512 in SHA-256 and SHA-512 refer. Youll find it at Finder Applications Utilities Terminal.
The former consists of the word value range of 32 words whereas the latter consists of the 64-bit word value. Secure Hash Algorithm 1 SHA-1 Secure Hash Algorithm 1 SHA-1 is a hash algorithm used to authenticate packet data. It normally takes you about 45 minutes to bring down and restart the server for maintenance.
Federal Information Processing Standard. The highest level of security. The server must be available on a constant basis and downtime in a given year cannot exceed 1 hour.
A database administrator verifies the issue and notices that the database file is now encrypted. AES Advanced Encryption Standard is fast and secure more so than 3DES. That means the following commands are identical.
Computation speed distinguishes General Purpose Fast Cryptographic Hash SHA-1 and SHA-2 alike from Slow Password Hash. A cybersecurity specialist needs to be familiar with the characteristics of the different types of malware and attacks that threaten an organization. SHA-1 SHA-1 is a hashing algorithm that produces a 160.
A hash function specified in FIPS 180-2 the Secure Hash Standard. SHA-2 is an algorithm a generalized idea of how to hash data. It was designed by the United States National Security Agency and is a US.
A Hash Value also called as Hashes or Checksum is a string value of specific length which is the result of calculation of a Hashing Algorithm. SHA-1 or Secure Hash Algorithm 1 is a cryptographic hash function which takes an input and produces a 160-bit 20-byte hash value. For example using SHA-1 to hash this online copy of Albert.
It works by transforming the data using a hash function. SHA-1 and MD5 are hashing algorithms. For NIST publications an email is usually found within the.
HOTSPOT You need to evaluate the output of the following code segment. SHA stands for Secure Hash Algorithm. Refer to PCI PTS FAQ and PCI DSS.
The Special Home Adaptation SHA grant is primarily intended for veterans who have lost the use of their hands are blind or have certain severe burns or respiratory injuries. SHA-1 is on the verge of breathing its last. The md5 command shows the MD5 hash of a file.
In cryptography SHA-1 Secure Hash Algorithm 1 is a cryptographically broken but still widely used hash function which takes an input and produces a 160-bit 20-byte hash value known as a message digest typically rendered as a hexadecimal number 40 digits long. Thats already quite lower than the network bandwidth. As part of some VPN software -- a router looks like a good candidate for running a VPN.
Cisco routers and the PIX Firewall use the SHA-1 HMAC variant which provides an additional level of hashing. Line numbers are included for reference only. It is a US.
IKE AH and ESP can use SHA-1 for authentication.

Learn Ranjana Newari Script Calligraphy Tutorial Script Learning
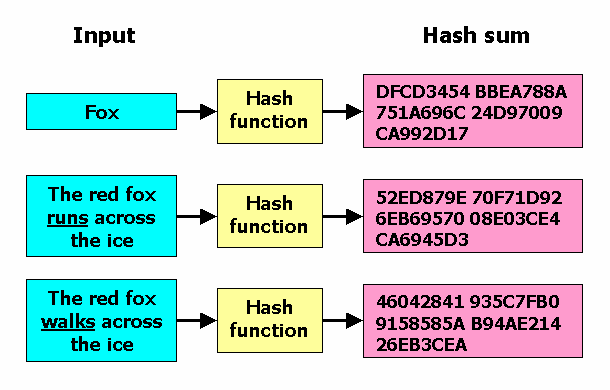
Md5 Vs Sha 1 Vs Sha 2 Which Is The Most Secure Encryption Hash And How

Revolutionizing Reminders Justice Quotes Islamic Quotes Prophet Quotes

Do You Have A Lot Passwords We All Do And At Times It S Pretty Hard To Remember Passwords Yet Alone Sha Password Printable Password Organizer Password Keeper
No comments for "For Which of the Following Purposes Would You Use Sha-1"
Post a Comment